What can we help you with?
Phishing Scams and Hacks
Last updated: July 1st, 2020
Phishing is scamming via impersonating individuals, organizations, operations, websites, etc.
Phishing is also the most common type of scam / attack on your funds in any cryptocurrency ecosystem. This is due to the low cost of attack and relatively high success rate.
This type of attack exploits people's inattentiveness when it comes to their security. Users generally prefer to have ease-of-use over security, so they're not used to having to validate that they're using the correct service, or interacting with the correct person or organization.
There are tools that help to mitigate this, so ultimately, phishing is effective for attackers because users undervalue security until something happens to them that compromises their funds.
Phishing via Website
How Is This Done?
An attacker copies the code from one of their favorite interfaces/exchanges/organizations. Then, they create a website with a similar URL to the one they're trying to impersonate, using the copied code.
After that, all they need to do is advertise their website for others to see and get tricked into using.
The Correct URL
vs.
The Phishing URL
How Can I Mitigate This?
In the example above, note the differences between the URLs. The phishing URL does not have the correct MyCrypto LLC. certificate specified.
Practice safety by validating the crypto-related websites that you use. Check the URLs to make sure that they are identical to the legitmate sites. Be aware that phishing URLs can use special characters to appear to have the correct spelling.
These special characters are added using something called Punycode.
Additionally, you can download the EtherAddressLookup Chrome extension, which will block phishing websites for you.
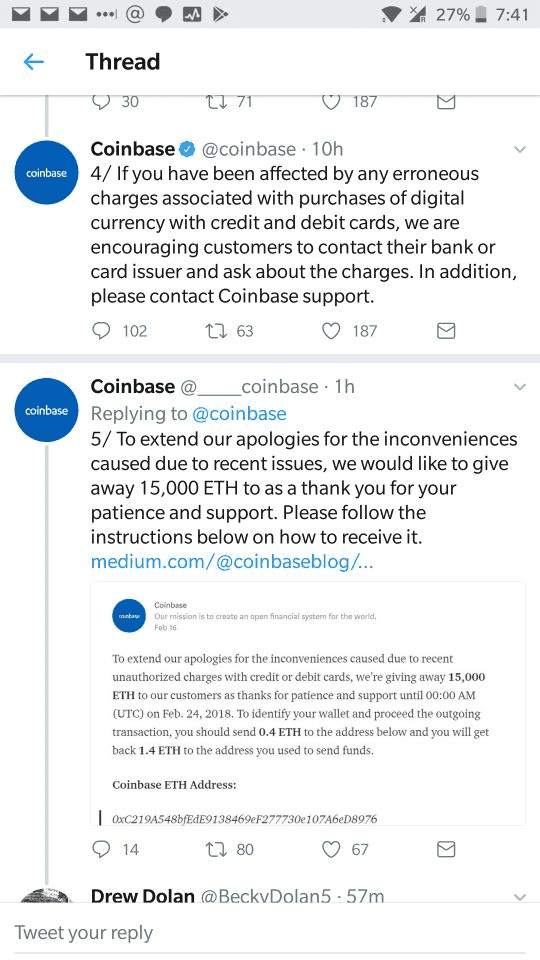
Phishing via Twitter
How Is This Done?
An attacker uses a Twitter account and changes the display name to impersonate crypto-related people/organizations like Vitalik Buterin, MyCrypto.com and ShapeShift.io. Then, they proceed to create an offer for the impersonated account's followers, trying to claim that they're giving out handouts, like so:
How Can I Mitigate This?
Follow the Common Scams Tips and do not attempt to get free money by sending money to others. It will not work.
Phishing via Mobile App
How Is This Done?
An attacker creates an app using logos and names of popular online tools like MyCrypto and MyEtherWallet. Then, they publish this app to an app store like the Google Play Store. If anyone enters their private keys into the app, the information becomes accessible to the attacker. The attacker can then siphon funds off whenever they want to.
Mobile phishing applications will appear in the mobile app store, masquerading as mobile versions of popular web-based tools, as pictured below.
How Can I Mitigate This?
Confirm that any mobile application you want to download for your phone is a legitimate application by verifying with the broader community on public forums.
How Can I Help Others to Not Fall for These Types of Scams?
Report scams like this to EtherScamdb.info. Furthermore, when you find these scams, post about them on social media sites like Reddit and Twitter so that users can learn about their existence. You can also share this article using the sharing links below the title.
If you don't understand any of the terms in this article, please try referencing our Ethereum Glossary.
Didn't find what you were looking for? Contact Us
MyCrypto is an open-source tool that allows you to manage your Ethereum accounts privately and securely. Developed by and for the community since 2015, we’re focused on building awesome products that put the power in people’s hands.
Donate
Subscribe to MyCrypto
Get updates from MyCrypto straight to your inbox!
By submitting your email, you affirmatively agree to our Privacy Policy